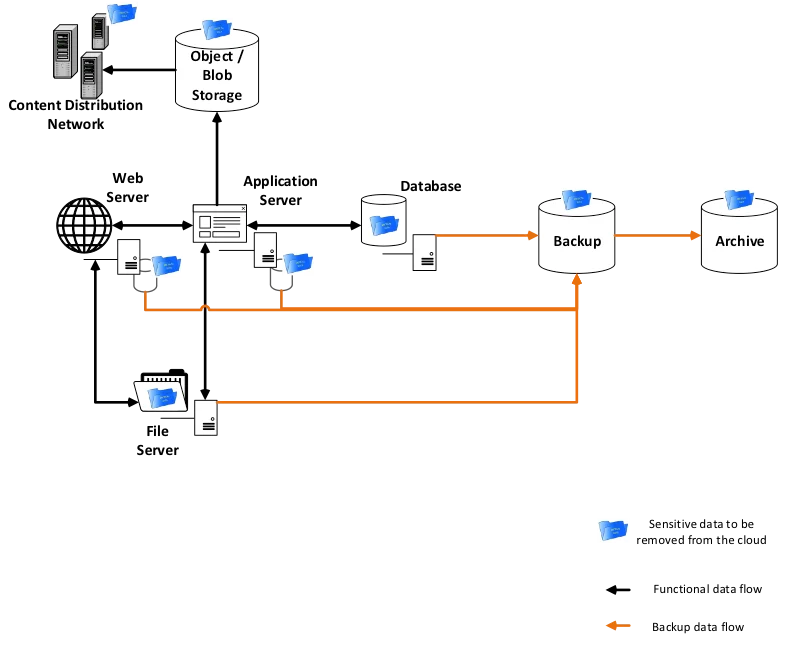
The digital landscape is undergoing a seismic shift. Businesses are increasingly embracing cloud computing, driven by its unparalleled scalability, agility, and cost-effectiveness. A recent Flexera 2023 State of the Cloud Report reveals that 95% of enterprises now leverage multiple cloud environments, highlighting the ubiquitous nature of cloud adoption. Why Cloud Security is Crucial for Your Business?
However, this migration to the cloud introduces a new set of security considerations. Unlike traditional on-premises infrastructure, cloud environments share responsibility between the cloud service provider (CSP) and the organization. This necessitates a proactive approach to cloud security to safeguard sensitive data, applications, and workloads.
Why Cloud Security Matters
Cloud security encompasses the measures taken to protect information, systems, and assets residing in the cloud environment. While CSPs offer robust baseline security, the onus of securing data and applications within the cloud falls on the organization.
Here’s why cloud security is crucial for your business:
- Data Breaches: Cloud environments are prime targets for cybercriminals due to the vast amount of sensitive data they store. According to the IBM Cost of a Data Breach Report 2023, the global average total cost of a data breach reached a staggering $4.35 million (IBM Security), highlighting the immense financial repercussions of a security lapse.
- Compliance Concerns: Many industries have strict data privacy regulations, such as GDPR and HIPAA. Organizations migrating to the cloud must ensure their chosen CSP and security practices comply with relevant regulations to avoid hefty fines and reputational damage.
- Loss of Control: Shifting to the cloud can lead to a perception of reduced control over data and systems. A well-defined cloud security strategy mitigates this concern by establishing clear ownership and accountability for security measures.
Common Cloud Security Threats and Vulnerabilities
Understanding common security threats empowers organizations to prioritize their security posture. Here are some key concerns to address:
- Misconfigurations: Inadequately configured cloud resources, such as storage buckets or virtual machines with open access, can create vulnerabilities that attackers can exploit.
- Insecure APIs: APIs (Application Programming Interfaces) are essential for cloud application integration, but they can also be entry points for unauthorized access if not properly secured.
- Insider Threats: Disgruntled employees or compromised accounts can pose a significant threat, highlighting the importance of robust access controls and identity management.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm cloud resources with traffic, rendering them unavailable to legitimate users.
Developing a Robust Cloud Security Strategy for Your Migration
A secure cloud migration begins with a well-defined cloud security strategy. Here are the key components:
- Cloud Security Planning: Conduct a thorough security assessment of your on-premises environment to identify potential vulnerabilities and data classification requirements. This information will guide security decisions during migration.
- Cloud Security Framework: Utilize established frameworks like NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) or CIS Controls to provide a structured approach to cloud security. These frameworks provide a roadmap for identifying, prioritizing, and implementing essential security controls.
- Cloud Security Policies: Develop clear and concise cloud security policies that outline acceptable use, access control procedures, and incident response protocols. Ensure all employees involved in the cloud migration and ongoing management understand these policies.
- Cloud Security Controls: Implement a layered approach to cloud security that incorporates access controls, data encryption, network security measures, and continuous monitoring and logging.
Key Cloud Security Measures to Implement During Migration
- Cloud Access Management (IAM): Implement granular IAM controls to restrict access to cloud resources based on the principle of least privilege. This ensures that only authorized users have access to specific resources they need to perform their job functions.
- Cloud Data Encryption: Encrypt data both at rest (stored in the cloud) and in transit (during transfer) to safeguard its confidentiality and integrity. Utilize encryption solutions offered by your CSP or implement third-party tools.
- Cloud Network Security: Implement cloud firewalls and network segmentation to control traffic flow within the cloud environment and restrict unauthorized access to sensitive resources.
- Cloud Monitoring and Logging: Continuously monitor your cloud environment for suspicious activity and security events. Leverage cloud provider logging services and configure alerts to promptly identify and address potential threats.
Ensuring Continuous Cloud Security Post-Migration
Security is an ongoing process, not a one-time event. Here’s how to maintain a strong cloud security posture after migration:
- Cloud Security Maintenance: Regularly update cloud resources, applications, and operating systems to patch vulnerabilities and address evolving security threats.
- Cloud Security Updates: Stay informed about the latest cloud security threats and updates from your CSP. Many providers offer security bulletins and advisories to keep customers informed about potential risks and mitigation strategies.
- Cloud Security Compliance: Regularly audit your cloud environment to ensure compliance with relevant data privacy regulations and internal security policies.
- Cloud Security Monitoring: Continuously monitor for suspicious activity and security events. Leverage automation tools for log analysis and threat detection to streamline security operations.
- Security Awareness Training: Educate your employees on cloud security best practices, including phishing awareness and password hygiene. Regular training empowers employees to identify and report suspicious activity.
Cloud computing offers a plethora of benefits for businesses of all sizes. By prioritizing cloud security and implementing a robust security strategy, you can mitigate risks and unlock the full potential of the cloud. A secure cloud environment fosters trust with customers, partners, and stakeholders, allowing you to leverage the power of the cloud with confidence.
Security is a shared responsibility in the cloud, but you don’t have to go it alone. Integra’s team of cloud security experts possesses the knowledge and experience to guide you through every stage of your cloud migration journey. We can help you assess your security posture, develop a customized cloud security strategy, and implement best-in-class security measures to ensure a smooth and secure transition.
Ready to embrace the cloud with confidence? Contact Integra today to learn how our cloud migration expertise and unwavering commitment to security can empower your business to thrive in the cloud landscape. Together, we can ensure your cloud migration is a success, unlocking the full potential of the cloud for your organization.